Tutorials
 The HackSuite has lots of hidden features that allow you to expand the program even further. You can learn more about the structure of the HackSuite and how to create new add ons for it by reading the tutorials.
The HackSuite has lots of hidden features that allow you to expand the program even further. You can learn more about the structure of the HackSuite and how to create new add ons for it by reading the tutorials.Create a vulnerability scanner module
The Plan
Let's do something cool, we will make a new module and not just some new module, nope let's make a fully automatic injection script!
This tutorial is the first step into making this. Let's first explain what we're going to do in two steps:
- make a new module called THC Inject IT(THC_II)
- make a callback that can bridge THC_DO and THC_II
Not so excited?
Well you should, let me tell you what the plan is and what's so special about this.
THC_SS' callback will trigger THC_DO to scrape urls that match a dork(in this case exploitable websites), when done THC_SS will tell THC_II to read out all the urls and find vulnerable websites.
So yes this is really exciting as it automates a time consuming job with a minimum of effort. Sounds nice huh, but hey, I haven't even created THC_II so let's start on that first.
If you haven't read the documentation about modules I suggest you do now.
First we will make a default module without anything fancy, use the documentation as a guideline.
Once finished you will have a module with two files:
- index.php
- setup.php
Also the module will now be listed in the projects list (development > list projects):
Using the file manager for THC_II (development > list projects > THC_II > file manager) we can add two new folders:
- logs: store the logs in here(will also be used to add extra log files for callbacks)
- targets: files with urls on a separate line
What will the module do?
Now that we made a basic module, let's think of what exactly we're going to create.
- we will make a vulnerability scanner for basic sql injections, rfi,lfi and xss
- possibilty to add custom exploits
- module must be able to run as a task in the background
- module will show results in realtime in an iframe
- module must be able to read a file with urls on every line
- module can poison parts or the whole of the query
- module will scan the response in order to see if the site is possibly vulnerable
- module will log possible vulnerable websites
Note: Will probably also make a commercial version with proxy support.
The Code
First we need to create the vulnerability scanner itself and afterwards integrate it into the suite.
In order to detect vulnerable websites we have to craft a specific input, poison the query and fire it to the target website:
- xss: <img src="somesite.ext" border="0" /> and see if the img tag gets through any html filter (we don't want to use a script right away)
- rfi: append some website eg Google and see if it is "included"
- lfi: try to include /etc/passwd and see if there's an error or if the list gets included
- sqli: trigger an error using quotes
Should be easy enough, let's start with this first.
As you can see I store the trigger(payload) and response(string to scan for) in an array to make it easier accessible and leave the opportunity to expand the file with different exploits.
You can save this as inject.php (you don't have to because I already made the module for you), let's proceed.
This is a good start to build the tool around. So what do we need next? Well we need a function that will target the destination url, send our cute payload and get the response.
This is what I came up with:
Now that we have a way to make a connection, there's only one thing left to do before we're going to put the code together. This is pretty much all the code you need to make a working scanner.
But in our case we want to build a user friendly application, don't we? So let's make the form, but what do we need?
mass scan options
- exploit selection menu, where you can select what exploits you want to try
- selection menu where you can select a file that contains target urls from a directory
- use a log file option
single url scan options
- exploit selection menu, where you can select what exploits you want to try
- single url input to scan
- use a log file option
- select which part of the query to inject
We're going to make the form interactive using a bit of jQuery. But first we're creating the form and store all output in $sCode, this is mandatory to do(if you don't know why please read the documentation).
The form will be a bit different than a normal html form, in this case we want to use screen files(basically an iframe that shows output in realtime). Let's first make a basic form and then add extra options later on:
Let's break down the code very quickly, because there's still a lot of things to do. When you look at the code you can see that it starts with defining an iframe using the $_CONTEXT['screen'] variable. This will be the iframe we're using to keep track of the attack in realtime, always use this style to define iframes.
Next the html is being buffered that contains the form and the div table, at the start of this you can see the following two lines of code:
$sCode = "<form method=\"post\" target=\"".$_CONTEXT['screen']['name']."\" action=\"".$_CONTEXT['screen']['src']."\">\n";
$sCode .= "<div class=\"moddesc\"><img src=\"./".$_CONTEXT['module_current']."/".$_CONTEXT['module_current'].".png\" width=\"90\" align=\"left\" /><h2>".$_CONTEXT['modules'][$_CONTEXT['module_current']]['name']."</h2>".$_CONTEXT['modules'][$_CONTEXT['module_current']]['description']."</div>\n";
This creates the header with the description and tells the browser to send the form to the iframe. If you would open the index.php and overwrite it with the code above, this would be the result:
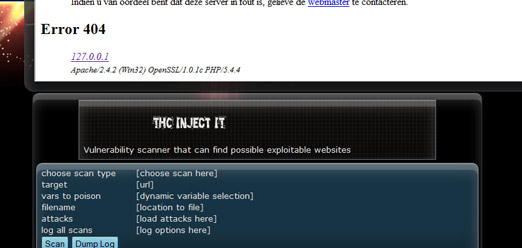
As you can see, we miss the png image in the header, the screen.php(iframe source) and the form input fields.
The rest of the code is self explanatory I think, notice the divs with ids. These will be used to show the proper options in the form using jQuery(hide/show based on selections in the form).
Now that we've created a basic form we need to fill in the rest of the html fields, create the javascript, and then we can start on the last part of the script(the handler of the form).
Here's the final version of the index.php
...and here's the jquery that is used to make the form dynamic. As I assume you can tell from the code what it does, there's no need to explain.
Now, we have only two files left to make:
- screen.php
- thc_ii.png
We will start of course on the php file.
First we will be making a test screen.php to see if everything goes as expected:
This can also be used as a template to build your screen files that support tasks and run in the background. Now that we have a template let's create the functional code that makes the injection script work.
I will be using three functions for the attack:
- ExploitUrl: create the exploiturl
- PayloadSend: creates a curl session with the remote server that sends the polluted parameters
- ParseResponse: parse the response of the server and see if the exploit was successful
func_exploiturl.php
func_payloadsend.php
func_parseresponse.php
Adding some more functions and putting the code together, this is what I came up with:
Now you have a working version of the injection/vulnerability scanner. You can add custom exploits as well by editing the inject.php file.
the image
Now we only need to create an image for the module. If you want to release your own module and let it be featured in the hacksuite versions, then this is mandatory.
What do we need:
- we need a recent version of photoshop
- we need a photoshop action, download here
- image must be a transparant png-24 file
- dimensions must be, width:125px and height:100-110px
- image must be named after the module name, in this case thc_ii.png
- image must be placed in the module
Seems like a whole list but I promise it's only a couple of minutes of work. In order to use the action, load the action and put buttons mode on.
You have full freedom to create your design.
The Result
The result is THC_II.


